Phishing Scams In April 2022: What To Watch Out For
As of the writing of this on the 8th April, 2022, there have been some new significant findings on how people will use phishing scams online. These are possibly the most convincing ones yet, and the hardest to identify. In this blog, we will investigate the latest tactics used by cyber criminals to give people a false sense of security so that they hand over their data.
We will be specifically highlighting two attacks in this blog, one that is targeting holidaymakers in Britain, and another that to most people, will be completely “invisible”.

TUI Holiday Phishing Scam
The holiday brand TUI has sent out a warning to holidaymakers via Twitter after they were made aware of phishing scams that target their customers.
Their Tweet states: “IMPORTANT We’re aware of a phishing scam targeting TUI customers on Twitter. Please do not send any personal information to email addresses given to you by other users. If you’re unsure, please contact us here or via Live Chat and we’ll confirm if the address is genuine.”
🚨 IMPORTANT 🚨
We’re aware of a phishing scam targeting TUI customers on
Twitter. Please do not send any personal information to email addresses
given to you by other users. If you’re unsure please contact us
here or via Live Chat and we’ll confirm if the address is
genuine.— tuiuk (@TUIUK) March
23, 2022
In the FAQ section of their website, TUI points out that they’re “aware that criminals are pretending to be TUI or TUI colleagues to try and defraud our customers using social media, email or telephone calls. To protect yourself against fraud never give away information about your booking on an email or telephone call.”
They have also identified the email address “covid-19@tuicustomercare.co.uk “as a main source of these scam emails. They have also noted that the websites “firstchoicekltd.com” and “tuicareteam.com” have been used to scam potential customers.
This warning has come at a time where there has been an increase in the planning of holidays, with TUI actually reporting that they have received 6 million bookings since 2022 began. This is a 20% increase on the numbers that they were getting pre-COVID, which isn’t really a surprise considering that people are using spring/summer to take breaks and make the most of the lack of travel restrictions that we have since COVID has calmed down.
Hackers have been promoting fake deals on social media, usually offering flights or hotels at low prices. This will catch the eye of some people, and they will be lead to a fake version of TUI’s website, which will make them think this is a genuine offer. People in Britain should keep an extra eye out, as easter and the Queen’s Jubilee are coming up, which both are four days weekends, which hackers will target as a lot of people will be wanting to get away during these times.
TUI have said that anyone who believes they have been scammed should contact Action Fraud to get this resolved as quick as possible.

Browser-In-The-Browser Attacks: A New Threat
A researcher for cyber security has discovered a new technique used by attackers that will make the scams impossible to detect using the usual advice given to avoid phishing attempts.
This method has been named BitB (browser in the browser), and this will fake a pop up of a single sign on window, using websites such as Google and Facebook. These pop ups will look basically identical to the genuine login pages and can easily trick people into handing over their personal information.
So, what makes these phishing attempts so hard to spot? To start with, the hackers have actually paid for an SSL Certificate, meaning that the domain is “https”, which highlights that the information on the website is encrypted, which is generally a sign that the website is legitimate and safe. Anyone can purchase an SSL Certificate however, so this means that the “https” isn’t always safe anymore.
These pop-up attacks replicate a single sign on page almost perfectly. Threatpost spoke to a cyber security researcher, that provided information on how this could have been performed. Facebook was used as an example by the researcher, known as “mr.d0x”, which showed how to create a mirror image of a single sign on page.
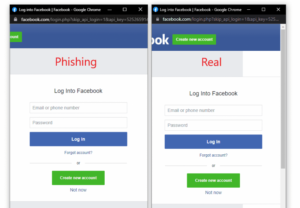
You only need a basic understanding of HTML/CSS to create a page like this, according to “mr.d0x”. These pop ups replicate a browser window within the browser and will use the exact same design as the legitimate website.
One strategy of avoiding nasty links is to hover over the URL to check the real destination of the page, but “mr.d0x” noted that BitB attacks can even fool people that use this technique. He explained that “If an onclick event that returns false is added, then hovering over the link will continue to show the website in the href attribute but when the link is clicked then the href attribute is ignored.”
This is a very sophisticated and scary attack, that really shows how important and effective password tools are at protecting uses from scams.
If you would like more information about phishing scams, check out our blog here on “Ten Red Flags For Spotting A Phishing Email”.